Using Secure Login with Yubikey

Introduction
More and more customers were asking us if the Secure Login plugins support more than mobile phones as the second factor. The reason behind that question is, not all their employees have a smartphone, they could use. And even with a "bring your own device" policy in place, work council rules and regulations can prevent you from using your personal smartphone. With 80 consultants out in the field and round about 40 employees in our branch offices, we know this issue on our own. Almost every single of our consultants has a smartphone available, but the other employees most often do not have.
The first feature we added to Secure Login to address this issue, was the support of white- and blacklists based on user groups and IP ranges. With this functionality, you can configure Secure Login, so that the employees working in the secure internal network, do not need the second factor, to access Jira and Confluence.
But this solves the issue only partial. And so with Version 1.3.1 of Secure Login for Jira and Version 1.1 for Confluence, we added a little feature, that will enable you to use a more wide range of authenticators. This blog post will introduce you to one of these newly supported authenticator alternatives: the Yubikey.
What is Yubikey?

Yubikey is a small smart USB-based authentication key, which supports a broad range of security and authentication protocols. One of these protocols is the OATH-TOTP standard, which is used by the Secure Login plugins. Corresponding the Yubikey serves as the second factor.
The USB key by itself gets identified as a keyboard when you plug it into a computer. The reason for this is that the key has a little button, which is used for other authentication protocols, like U2F. That means, the Yubikey does not work as a USB storage device and you can not access it directly. But anyway, the secret key, needed to generate the PINs for Secure Login is stored on the key. So you can easily use the device on different computers.
Installation
To use the Yubikey as the second factor with the TOTP protocol, a little piece of software must be installed on the computer. The software is named "Yubico Authenticator" and can be downloaded in the software section on the website of the producer Yubico. The good news is, you do not need administration privileges on the system, you want to install it on. And there are versions for different operating systems available. So if you are like me, working on a bunch of different computers, with some not being able to install software on, you can use the Yubikey anyway. Just install the software into the temp folder or somewhere else, where you have permission to write.
Configuration
Once you have installed and started the software, you are ready to go and configure it for the usage with Secure Login. After logging in, into the Jira or Confluence instance with your username and password, you get redirected to the Secure Login registration page. Just click on the "Problems scanning the QR code?" link, and you will see a panel with your secret code, like in the screenshot below.
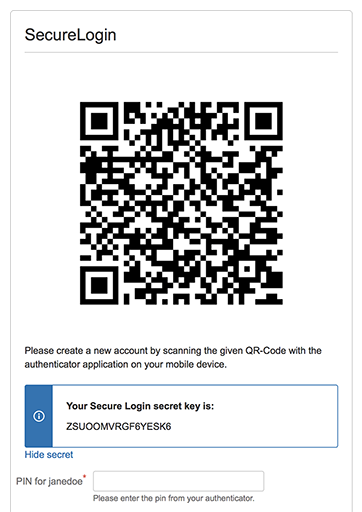
Next, select the code and copy it to the clipboard. Afterward, you open the "Yubico Authenticator" application and add a new entry via "File->Add...".
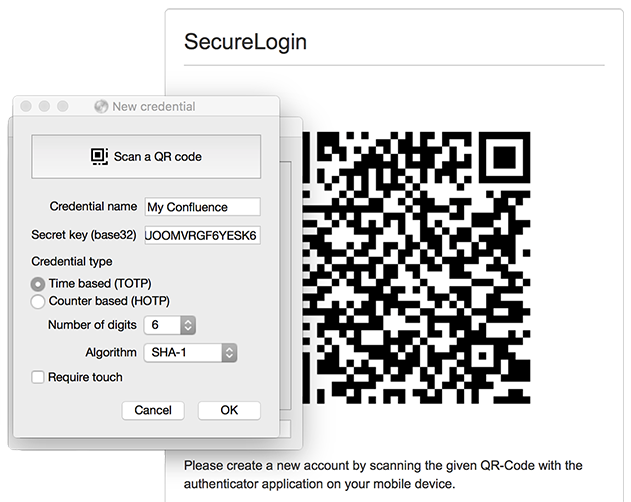
Thankfully the default values in the authenticator already fit the requirements of Secure Login. And so you just have to give the entry a speaking name, helping you to recognize which application this entry is for, and paste the secret key into the intended field. Finally, press the OK button to save and finish the configuration.
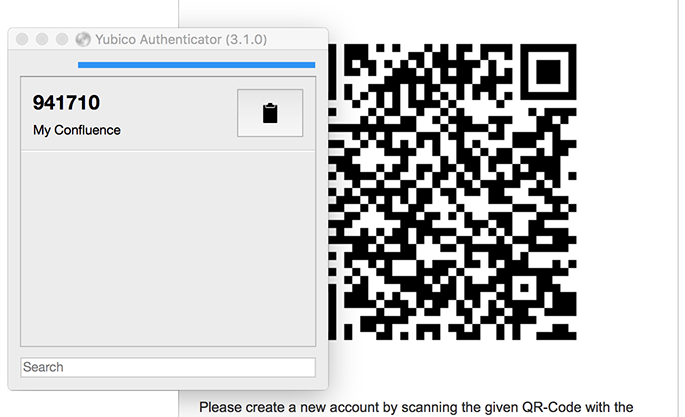
Back in the main window of the "Yubico Authenticator" you will see the created entry now, and the application shows you a 6-digit pin, which will change every 30 seconds. Copy this pin to the clipboard, switch back to your Jira or Confluence instance, and paste it in the PIN field. Confirm the registration by pressing the OK button, and you successfully registered your Yubikey for using with your system.
Summary
If you or your employees do not have a smartphone available and still want to use a two-factor authentication with your Jira or Confluence system, the Yubikey is a good and valid alternative. Compared with other hardware-based authenticators, which uses a hard encoded secret in the device, there is no need for an expensive inventory management of the devices. If the Yubikey gets lost, just revoke the user configuration for Secure Login and hand the user a new device. The next time the user logs in he/she just have to repeat the registration steps to activate the new key.
Also, the Yubikey can be used for multiple systems at once, each with a single dedicated secret and for other security purposes. For example, you can save your PGP private keys on the device too.
Have you additional question to the Secure Login plugin or the Yubikey? Feel free to contact us. Or meet us at the European Summit and AtlasCamp in Barcelona, this May, for a hands-on presentation of Yubikey and our plugin.
Dieser Blogpost wurde bisher 13213 mal aufgrufen.
Blogpost teilen
INSIGHTS!
Current topics fresh out of your head. We look forward to sharing and discussing them with you.
